Consultation with a Cybersecurity Engineer: Current Inquiries Regarding AI in Cybersecurity
In this ask-me-anything-style Q&A, leading Jobswifi cybersecurity expert Philip responds to colleagues’ questions on AI in cybersecurity and provides data and network protection tips and best practices.

CybersecurityArtificial IntelligenceSecurity Engineering
PREVIOUS ROLESenior Security Consultant
YEARS OF EXPERIENCE: 15
Philip is a cybersecurity professional and developer with wide-ranging experience in the government, defence, manufacturing, and finance sectors. A former cloud security architect at Hewlett Packard Enterprise, he now advises executive clients on planning, prioritizing, and executing strategic security initiatives.
Navigating Cybersecurity Frontiers: A Q&A with Philip With a wealth of experience spanning two decades in diverse cybersecurity roles across large corporations and startups, Ilia Tivin, Toptal’s cybersecurity advisor, brings profound insights into the past, present, and future of the field. This Q&A offers a condensed overview of a recent ask-me-anything-style Slack forum, where Tivin addressed inquiries about the role of artificial intelligence (AI) in the realm of cybersecurity, posed by fellow Toptal engineers and security professionals worldwide. Editor’s note: Some questions and answers have been edited for clarity and brevity.
Do you think modern cybersecurity requires AI solutions?
Yes, I do think AI will be required in the future. To be frank, AI’s capacity for creating exploits is fairly weak today. But that is going to escalate over time—and so should our defences.
The response hinges on the interpretation of a security breach. Adequately programmed AI can effectively pinpoint vulnerabilities by examining and sorting through code. Additionally, AI has the capability to craft highly convincing phishing emails, seamlessly incorporating specific details relevant to your organization. While I have not encountered instances beyond phishing emails, it is crucial to note that the absence of evidence does not necessarily imply non-existence.
Examples of AI in Cybersecurity Implementation
Are there specific AI-driven cybersecurity tools that you employ, and if yes, which ones do you endorse?
In fortifying the defences provided by clients’ conventional security solutions, I leverage the AironWorks phishing simulation platform. This tool facilitates the creation of tailored phishing simulations, enabling organizations to assess the preparedness and security awareness of their employees. However, concerning testing, I currently find that AI may not be optimally positioned to offer substantial assistance in the realm of cybersecurity. While major companies profess the integration of AI into their cybersecurity products, the practical utility of AI in this context varies significantly.
Can you suggest a fun website where security hobbyists can play around with and discover different topics of offensive or defensive security?
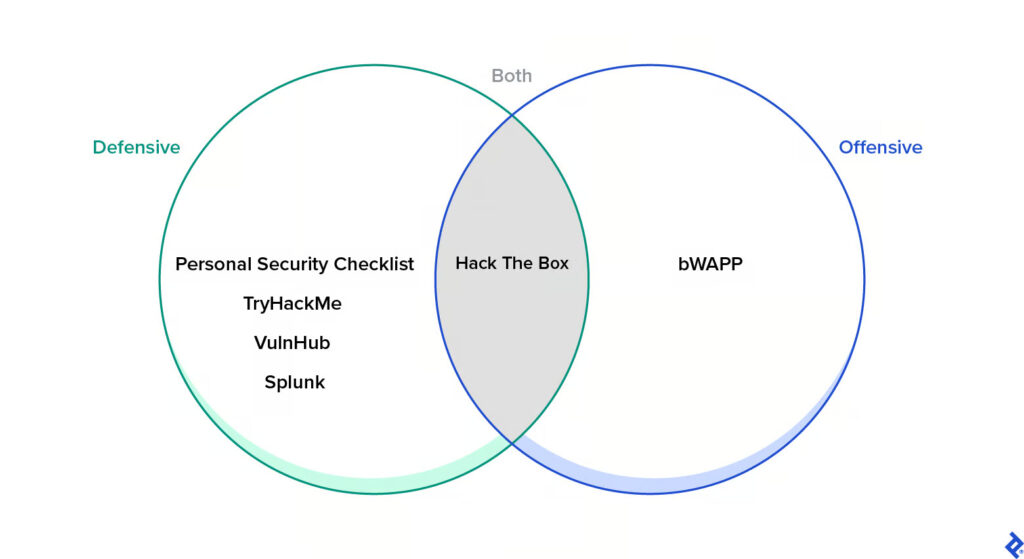
I, for one, am a big fan of personal security. From a defensive perspective, I always recommend the Personal Security Checklist, a GitHub list of 300-plus tips for protecting digital security and privacy. You can use TryHackMe as a way to get started in security, or even compete in some of its online challenges. VulnHub is awesome even if it’s not regularly updated. Challenges at Splunk—which appears ready for a refresh—come to mind. From an offensive perspective, bWAPP is a good Docker container that allows you to try to exploit a web application for yourself. And there’s also Hack The Box, which includes both defensive and offensive elements.
Differing Opinions on Mac Security: A Spectrum of Views
Views on Mac security vary, with some asserting that Macs are inherently secure, while others advocate for a cautious approach. What’s your take on the matter?
Divergent Perspectives on Mac Security: A nuanced exploration
The debate surrounding Mac security is multifaceted. Some argue that the lower number of Mac users compared to PCs makes them less susceptible to cyberattacks. However, others contend that Mac users’ higher average spending on their computers makes them an attractive target. Recent OS security fixes suggest a growing acknowledgement of the potential risks, as highlighted by a Wired article on the subject.
